New Release: The Gorilla Guide® To… Choosing the Right Data Masking Solution for DevOps Data
Malicious attacks on stored data are getting increasingly sophisticated, given the value of personal data to criminals who use it for identity theft, fraud, and other purposes. Therefore, responsible organizations are integrating techniques for data protection into the same processes they use for development and operations. The Gorilla Guide® To… Choosing the Right Data Masking Solution for DevOps Data covers the elements of a good data masking solution, explaining why each is important.
The concept of data masking seems simple: Keep your real data (hopefully encrypted) in a secure location, and change sensitive fields to garbage before you send the data to testers, researchers, and other users who need only a simulation of the data. Figure 1 illustrates how you can preserve real data while masking it for consumption by other organizations.
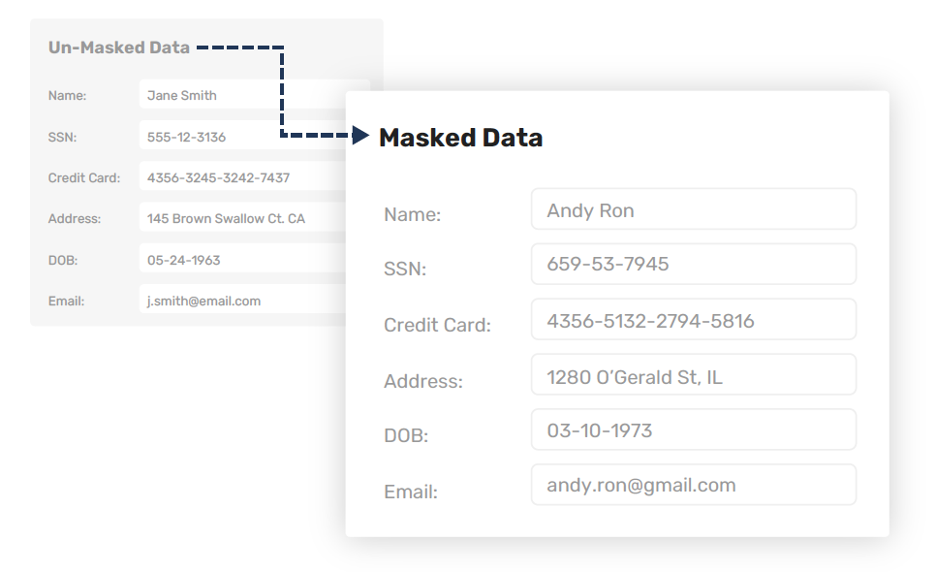
But there are many complications to this simple scenario. Regulatory requirements might require certain kinds of protection. Most organizations spread data across distributed environments and multiple cloud solutions. Databases require referential integrity—in other words, the masking must recognize how the data is used by the database and make sure that queries still work with masked data.
Traditional masking solutions are slow, under the assumption that new data is uploaded and shared only at fixed intervals. But modern environments update data on customers and events constantly. Not only do they need fast masking solutions, but these must be automated and easy to invoke through APIs.
The Gorilla Guide® To… Choosing the Right Data Masking Solution for DevOps Data shows how data masking can be integrated into workflows through processes commonly known as DevOps and be implemented through modern security policies known as zero trust. A good solution is both easy to use and highly secure.
Inside the Guide
Gorilla Guides make learning and discovery approachable and easy, and they take the guesswork out of navigating complicated IT technologies. Written by an industry expert, and brought to you by Delphix, this resource is packed full of trusted information about modern data protection!
Download the book and learn all about:
- Different Types of Data Protection, and Their Strengths and Weaknesses
- Why Data Masking Is Important, but Hard To Integrate into Your Workflows
- Why Data Masking Involves More Than Simple Data Replacement
Table of Contents
Introduction
Chapter 1: Understanding Why You Need to Mask Your Test Data
- What Is Masking and How Does It Address Customer Privacy?
- Why Is Masking Test Data Important?
Chapter 2: Recognizing What Features To Look for in a Masking Solution and Why They’re Important
- Key Features and Capabilities
- Comparing Common Approaches to Data Masking
Chapter 3: How a DevOps TDM Approach Can Help Your Organization
- Enable Zero Trust for DevOps Data
- Develop Applications Faster So You Can Digitally Transform
- Learn More
About The Author
Lawrence Miller, CISSP, has worked in information technology in vari- ous industries including military, telecommunications, legal, retail, and professional services for more than 30 years. He earned an MBA in Supply Chain Management from Indiana University and has written numerous books on technology and security topics.
About Delphix
Delphix is the industry leader for DevOps test data management.
Businesses need to transform application delivery but struggle to balance speed with data security and compliance. Our DevOps Data Platform automates data security, while rapidly deploying test data to accelerate application releases. With Delphix, customers modernize applications, adopt multi-cloud, achieve CI/CD, and recover from downtime events such as ransomware up to 2x faster.
Leading companies, including Choice Hotels, Banco Carrefour, and Fannie Mae, use Delphix to accelerate digital transformation and enable zero trust data management.
Learn more at delphix.com.