New Release: The Gorilla Guide® To… Securing Cloud Native Applications on Kubernetes, Foundation Edition
If your home has several doors, each increases your vulnerability to robbery. Modern containerized applications running on Kubernetes are in a similar situation: Each door into the application needs one or more guardians, and you have to monitor each guardian to make sure they’re awake and properly armed.
In The Gorilla Guide® To… Securing Cloud Native Applications on Kubernetes, Foundation Edition, Dan Sullivan neatly divides up the tasks administrators and developers need to perform.
For instance, are you unclear where authentication takes place? Kubernetes actually rests on two common types of authentication. One is done on the cloud service, using passwords and assigning roles to groups of users through identity and access management (IAM). The other is performed by Kubernetes, using certificates and tokens to grant access to your container.
Sullivan treats security as four layers: the cloud, cluster, container, and application code. Other layers (hardware, network, and operating system) are mostly handled by the vendor, but Sullivan points out that you still have several responsibilities at these layers (Figure 1).
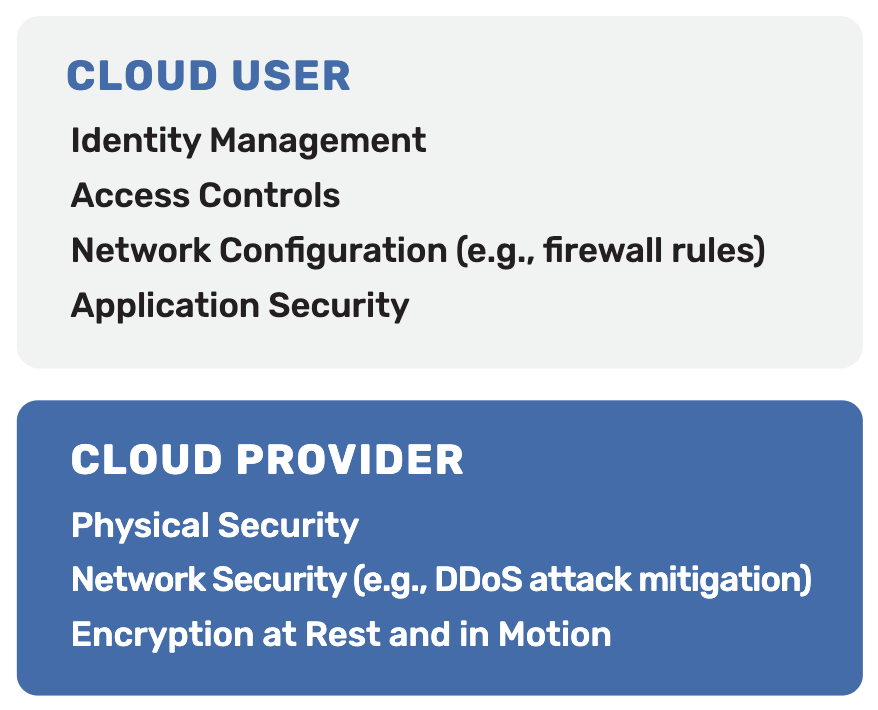
Although Sullivan doesn’t use the popular term “zero-trust,” that’s essentially the environment he’s recommending. Containerized applications consist of many cooperating pieces, so each and every connection between them requires encryption, authentication, and other security. Read this concise guide for a comprehensive list of measures that protect you and your end users.
Inside the Guide
Gorilla Guides make learning and discovery approachable and easy, and take the guesswork out of navigating complicated IT technologies. Written by an industry expert, and brought to you by Kasten by Veeam, this resource is packed full of trusted information about container security!
Download the book and learn all about:
- The 4 C’s of Kubernetes Security
- Best Practices & Tools: Evaluating Security Controls Against Benchmarks
- Ensuring Kubernetes Application Security
Table of Contents
The 4 C’s of Kubernetes Security
Cloud Native Security
Cluster Hardening
Container Security
Code Security
Evaluating Security Controls Against Benchmarks: Best Practices and Tools
Ensuring Kubernetes Application Security Requires Vigilance
About the Author
Dan Sullivan is a principal engineer and architect specializing in cloud architecture, data engineering, and analytics. He has designed and implemented solutions for a wide range of industries, and writes widely on various IT infrastructure topics.
About Kasten by Veeam
Kasten by Veeam® is the leader in Kubernetes backup. Kasten K10 is a Cloud Native data management platform for Day 2 operations. It provides enterprise DevOps teams with backup/restore, disaster recovery and application mobility for Kubernetes applications. Kasten K10 features operational simplicity, and integrates with relational and NoSQL databases, all major Kubernetes distributions, and runs in any cloud to maximize freedom of choice. Our customers are confident that their Kubernetes applications and data are protected and always available with the most easy-to-use, reliable and powerful Cloud Native data management platform in the industry. For more information, visit www.kasten.io or follow @kastenhq on Twitter.