New Release: The Gorilla Guide to…® Ransomware for Govies

Ransomware attackers aren’t known for their compassion. For instance, they love to tie up hospital records—which could lead to the deaths of patients—precisely because that data is so precious and so urgently needed. Because of those characteristics, the attackers can demand more money and get it faster.
Governments are also juicy targets, possessing large amounts of money and running essential functions. Of course, an attack can backfire on a ransomware actor if they anger an organization possessing law enforcement capabilities—but if the cybercriminal is in a jurisdiction that’s hostile to the victim’s government, they might escape retribution. In fact, they may well be working for the hostile government that protects them.
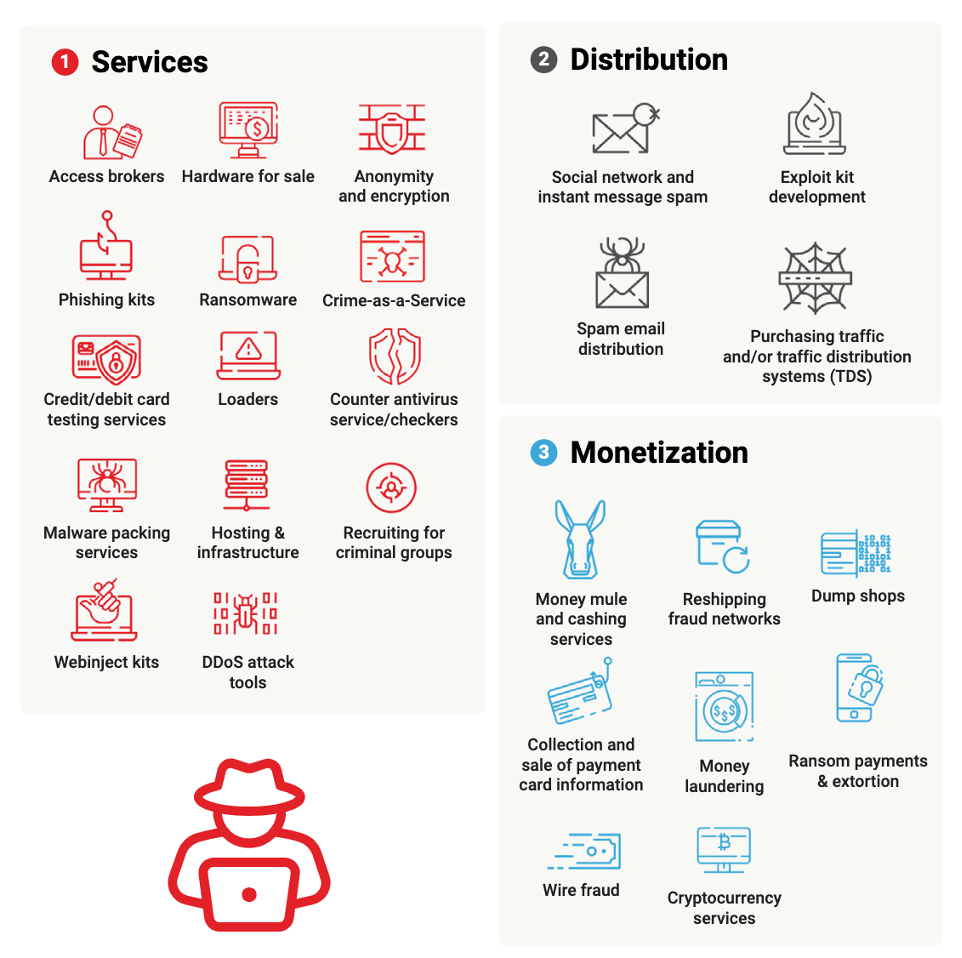
In Ransomware for Govies, Katherine Gorham offers a detailed description of ransomware’s history, methods, attack vectors (means of entering a computer system), risk factors, and complex business environment (see Figure 1), with an emphasis on government victims. She tells you where you can get expert help—which you should definitely employ before the attack occurs—and what preparations to make for the dreaded moment when you become a victim. She explains the high-level phases of protecting your assets: prevent, detect, respond, and predict.
Inside the Guide
Gorilla Guides make learning and discovery approachable and easy, and they take the guesswork out of navigating complicated IT technologies. Written by an industry expert, and brought to you by CrowdStrike, this resource is packed full of trusted information about protecting yourself from ransomware attacks!
Download the book and learn all about:
- Motivations That Drive Ransomware Attackers
- How to Check Your Organization for Vulnerabilities
- Available Help to Prevent or Recover from Attacks
Table of Contents
Introduction
Chapter 1: The Crime That Keeps Changing
- A Short History of Ransomware
- When It’s Not Just About the Money
- Know Your Enemy
Chapter 2: The World of Cybercrime
- Getting into Your Network
- The Patching Dilemma
- Moving Laterally
- The Rise of Big Game Hunting
Chapter 3: Why Crime as a Service?
- The Exploit Market
Chapter 4: The Ransom Dilemma
- Plan for the Worst
- Don’t Go It Alone
Chapter 5: Defending Yourself Against Ransomware
- Defense in Depth
- Get Help
Download Your Copy!
About the Author
Katherine Gorham is a writer and editor with a focus on information security. She excels at information synthesis and understands how all the pieces of complex modern information systems fit together …and how they can be vulnerable to attack.
About CrowdStrike
CrowdStrike, a global cybersecurity leader, is redefining security for the cloud era with an endpoint and workload protection platform built from the ground up to stop breaches. The CrowdStrike Falcon® platform’s single lightweight-agent architecture leverages cloud-scale artificial intelligence (AI) and offers real-time protection and visibility across the enterprise, preventing attacks on endpoints and workloads on or off the network. Powered by the proprietary CrowdStrike Threat Graph®, CrowdStrike Falcon captures upward of 1 trillion endpoint-related events per day in real time from across the globe, fueling one of the world’s most advanced data platforms for security.
With CrowdStrike, customers benefit from better protection, better performance and immediate time-to-value delivered by the cloud-native Falcon platform.
There’s only one thing to remember about CrowdStrike: We stop breaches.
Download your copy today!