New Release: The Gorilla Guide to…® Protecting the Modern Enterprise

Ransomware plagues organizations of all types. Why, then, a book devoted to education? Katherine Gorham lays out the reasons concisely at the start of Ransomware for Education, Express Edition: “Education institutions tend to be software monocultures, making them easy to attack. They also have lots of potential victims (students and teachers) who don’t know how to protect themselves from phishing or other scams. Other reasons are offered as well.”
Ransomware for Education, Express Edition is highly practical. Gorham points out the importance of keeping systems updated, so that attackers can’t exploit well-publicized security flaws, but also highlights why it’s hard to keep up with patches. She also weighs the pros and cons of cyber insurance.
The book starts with a summary of ransomware: how it operates, how it has evolved, the complexity of its infrastructure (Figure 1), how catastrophic its effects can be, and so on. Gorham describes two common entry points for attackers: phishing and files containing malware. (The two types of attack often go together.)
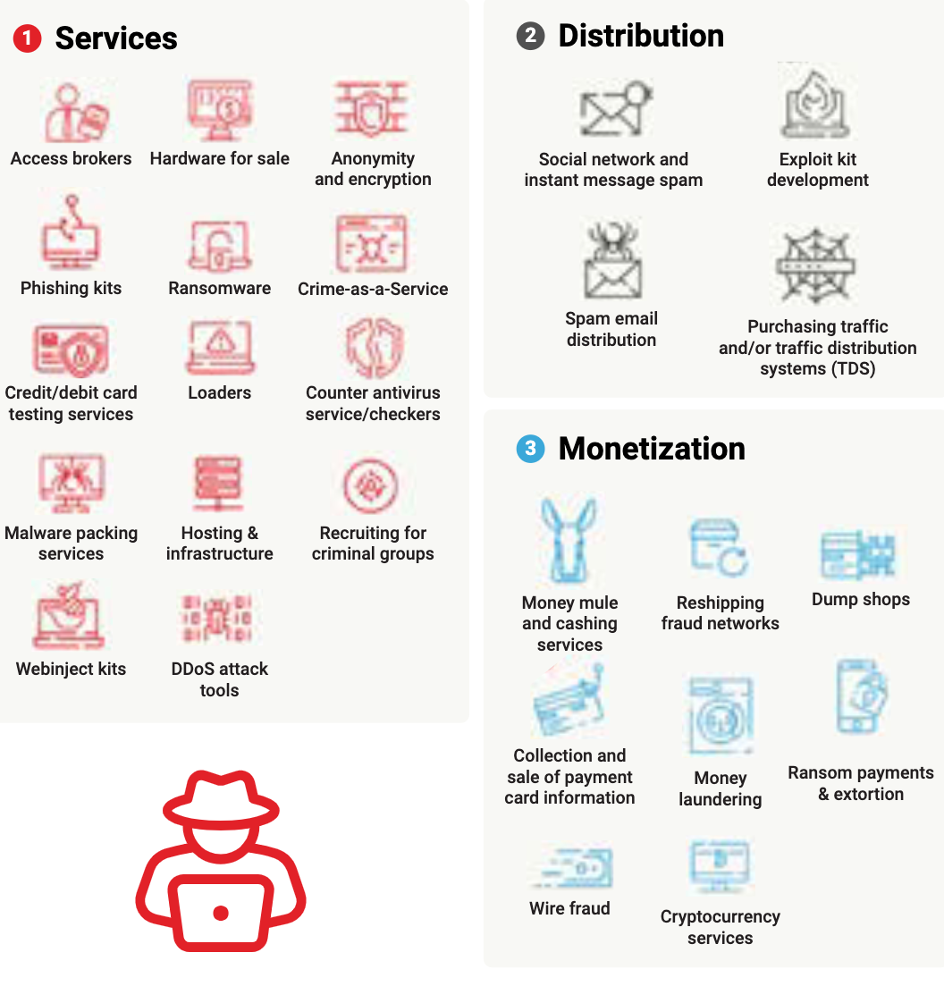
When ransomware attacks are successful, they create panic in many ways. First of all, in a modern world driven by software, an educational institution can be instantly crippled. Second, the ransomware attacker deliberately fosters a sense of urgency by insisting on tight deadlines for payment. Therefore, every institution must be prepared for an attack. Gorham lays out the elements of an incident response plan, outside organizations you should contact for help, and key elements of protection such as making a catalog of all devices used within your institution. There’s also information and advice on:
- Why no institution is too small or insignificant to suffer an attack
- The sophistication of ransomware attacks
- Stages in modern network defense
Inside the Guide
Gorilla Guides make learning and discovery approachable and easy, and they take the guesswork out of navigating complicated IT technologies. Written by an industry expert, and brought to you by CrowdStrike, this resource is packed full of trusted information about practical business security!
Download the book and learn all about:
- Why no institution is too small or insignificant to suffer an attack
- The sophistication of ransomware attacks
- Stages in modern network defense
Table of Contents
Introduction
Chapter 1: The Crime That Keeps Changing
- A Short History of Ransomware
- When It’s Not Just About the Money
- Know Your Enemy
Chapter 2: The World of Cybercrime
- Getting Into Your Network
- The Patching Dilemma
- Moving Laterally
- The Rise of Big Game Hunting
Chapter 3: Why Crime as a Service?
- The Exploit Market
Chapter 4: The Ransom Dilemma
- Plan for the Worst
- Don’t Go It Alone
Chapter 5: Defending Yourself Against Ransomware
- Defense in Depth
- Get Help
- Gain Intelligence About the Threats
Download Your Copy!
About the Author
Katherine Gorham is a writer and editor with a focus on information security. She excels at information synthesis and understands how all the pieces of complex modern information systems fit together, making them vulnerable to attack.
About CrowdStrike
CrowdStrike, a global cybersecurity leader, has redefined modern security with one of the world’s most advanced cloud-native platforms for protecting critical areas of enterprise risk — endpoints and cloud workloads, identity, and data.
Powered by the CrowdStrike Security Cloud and world-class AI, the CrowdStrike Falcon® platform leverages real-time indicators of attack, threat intelligence, evolving adversary tradecraft and enriched telemetry from across the enterprise to deliver hyper-accurate detections, automated protection and remediation, elite threat hunting and prioritized observability of vulnerabilities.
Purpose-built in the cloud with a single lightweight-agent architecture, the Falcon platform delivers rapid and scalable deployment, superior protection and performance, reduced complexity and immediate time-to-value.
CrowdStrike: We stop breaches.