New Release: The Gorilla Guide To…® Extended Detection and Response (XDR)!

A wave of automation has taken on the computing field in such areas as application testing and integration (DevOps), orchestration (for instance, Kubernetes), and deployment (for instance, autoscaling in the cloud). Nowhere is automation and intelligent orchestration more important than security, where the cost of a single data breach usually reaches into the millions of dollars, and where breaches are dangerously on the increase.
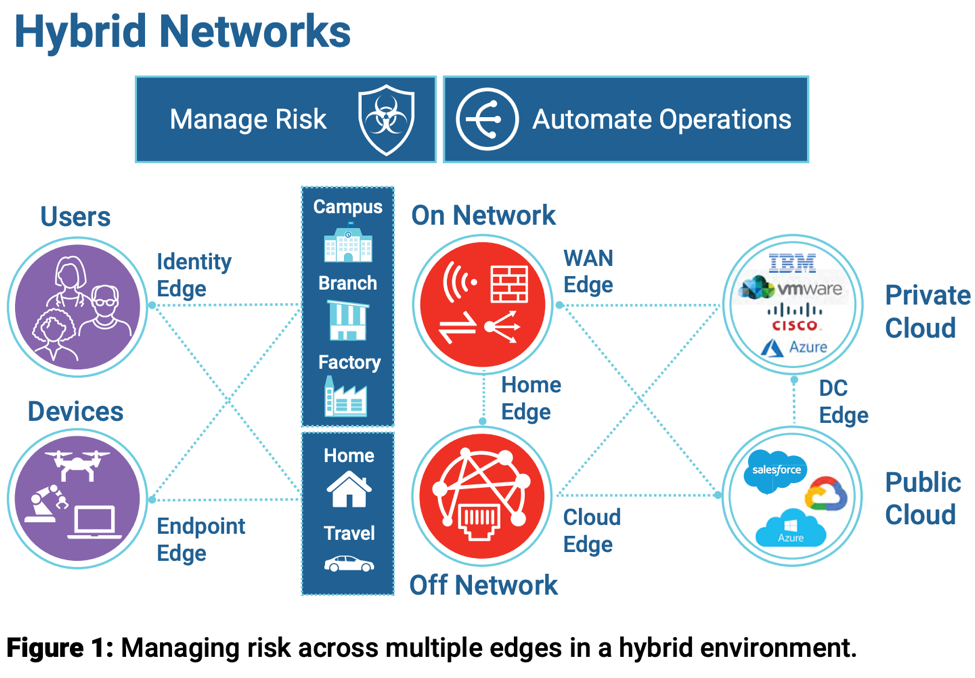
The complexity of modern network environments (see Figure 1) increases the area vulnerable to attack, and working from home (a trend not likely to go away after we tame the COVID-19 pandemic) has also offered numerous new services and network points that intruders can break into.
Extended Detection and Response (XDR) is a relatively new approach to system and network security. As described in this Gorilla Guide by Lawrence Miller, XDR is more sophisticated than traditional security information and event management (SIEM) or security orchestration, automation, and response (SOAR). Although all these tools can detect incidents and generate automated responses, XDR goes farther in coordinating different systems to work together.
Miller’s Extended Detection and Response (XDR) deftly introduces the topic and lays out the rationales and how it works, introducing Fortinet’s XDR solution at the end. The report is packed with collections of useful information, such as a list of certifications that XDR vendors should obtain, and a checklist for evaluating vendors
Inside the Guide
Gorilla Guides make learning and discovery approachable and easy, and they take the guesswork out of navigating complicated IT technologies. Written by an industry expert, and brought to you by Fortinet, this resource is packed full of trusted information about the role of XDR in modern monitoring and response!
Download the book and learn all about:
- The Importance of Automating Data Collection, Data Analysis, and Orchestration of Response
- How XDR Differs From Previous Security Solutions
- The Fortinet Solution
Table of Contents
Introduction: A New Way to Protect Your Data and Infrastructure
Chapter 1: Problems Solved
- The Digital Attack Surface Is Expanding
- Threats Are Increasingly Sophisticated
- Complexity in the Security Ecosystem Slows Response
- Operational Costs Are Increasing
Chapter 2: What Is XDR?
- Defining Extended Detection and Response (XDR)
- Cross-Product Incident Detection
- Incident Validation Through Enrichment, Analysis, and Classification
- Incident Remediation to Contain, Repair, and Return to Operation
Chapter 3: Various Approaches to XDR
- Open or Closed Systems
- Automation and Orchestration
Chapter 4: Is XDR Right for My Organization?
- Do You Have a Dedicated Team Monitoring Security Alerts?
- Do You Have the Expertise and Time to Investigate Potential Incidents?
- Do You Have a Defined Set of Response Processes That Are Specific to Your Organization?
- Is Your Security Staff Spending Time in the High-Value Roles You’d Like Them to Play?
Chapter 5: How to Decide Which XDR is Best for You
- Which XDR Solution is Best for Your Organization?
Chapter 6: The Fortinet Solution
- The Fortinet Security Fabric
- AI-Powered Extended Detection and Response
- Automatable Response
- Take a Fundamentally Different Approach
- Stay Ahead of the Curve
Download Your Copy!
About the Author
Lawrence Miller, CISSP, has worked in Information Security and Technology Management for more than 25 years. He is currently working as an IT security solutions consultant. He has previously worked as the Vice President of IT for a major Verizon reseller, director of IT and e-commerce for a retail merchandising company, and IT operations manager for a top-100 U.S. law firm. He is the author of more than 200 books on various topics including information security, cloud, unified communications and collaboration, storage, 5G, and the Internet of Things.
About Fortinet
Fortinet (NASDAQ: FTNT) secures the largest enterprise, service provider, and government organizations around the world. Fortinet empowers its customers with intelligent, seamless protection across the expanding attack surface and the power to take on ever-increasing performance requirements of the borderless network—today and into the future. Only the Fortinet Security Fabric architecture can deliver security without compromise to address the most critical security challenges, whether in networked, application, cloud, or mobile environments. Fortinet ranks number one in the most security appliances shipped worldwide and more than 450,000 customers trust Fortinet to protect their businesses.
Download the book here.